Google’s stringent oversight of Chrome extensions, including the requirement for verification before publication on its platform, has not proven to be a cure-all for issues related to malware or illicit activities perpetrated by third parties. Surprisingly, data theft, particularly the pilfering of passwords, continues to be within the realm of possibility.
A recent study conducted by the University of Wisconsin-Madison, as reported by BleepingComputer, has shed light on a disconcerting revelation. It suggests that passwords stored within a website’s source code are susceptible to extraction through specific methods employed by Chrome extensions.
This research underscores a concerning reality: Google’s browser seemingly affords an excessive degree of access to extensions, potentially enabling third parties to surreptitiously obtain data.
Websites that store user data, including usernames and passwords in unencrypted plain text within their HTML code, are particularly vulnerable. The crux of the issue lies in Chrome’s extensions, which are granted unfettered access to DOM Trees, thereby allowing them to scrutinize the contents of text input fields and even delve into the source code of websites.
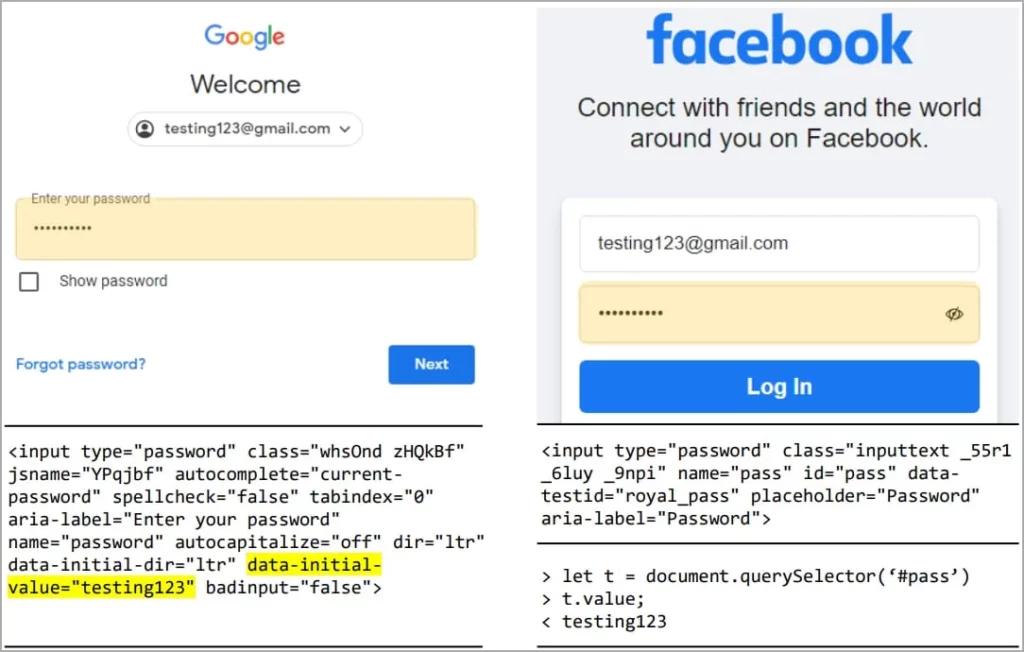
Moreover, these extensions can capture and record users’ keystrokes, effectively bypassing password security measures implemented on websites, including encryption protocols.
Despite Google’s implementation of the Manifest V3 protocol for Chrome extensions, which serves to prevent code of uncertain origins from running, it notably lacks any security mechanisms to control the interactions between extensions and websites.
As a result, an estimated 17,300 extensions, constituting approximately 12.5% of those available for the browser, possess the potential to exploit this vulnerability. This group includes a wide array of extensions, such as ad blockers and various shopping support applications, among others.

