GitHub, the code-hosting platform owned by Microsoft, has announced that it will require all developers who contribute code to any project on the platform to use two-factor authentication (2FA). This move is aimed at strengthening the software supply chain against cyber attacks. GitHub had previously announced in May 2021 that it planned to make 2FA mandatory by the end of 2023.
However, it started the process earlier that year by enforcing it on the top 100 packages, and later in November, on other high-impact packages. High-impact packages are defined as those with over 1 million weekly downloads or more than 500 dependents.
Starting March 13, 2023, the platform will enforce 2FA platform-wide. The process will be rolled out incrementally to different groups of developers and project administrators throughout the rest of the year.
With this move, GitHub aims to improve the security of the platform and mitigate the risk of cyber attacks that could compromise the integrity of the codebase. By requiring 2FA, the platform can ensure that only authorized contributors have access to the code repository, making it more difficult for attackers to compromise the software supply chain.
GitHub Rolls Out Mandatory Two-Factor Authentication for Developers
GitHub, a pivotal player in the global software supply chain with over 100 million developer users, is implementing mandatory two-factor authentication (2FA) to improve software supply chain security. Recent high-profile attacks, such as the SolarWinds breach in 2020 and the Log4Shell security flaw, have brought the issue to the top of political agendas worldwide. In response, the Biden administration issued an executive order in 2021 to secure the country’s cyber defenses and published a new cybersecurity strategy last week. This includes calling on Big Tech to shoulder more responsibility for ensuring robust systems, something that mandatory 2FA will aid.
Open source software has been a major focus of the administration’s cybersecurity efforts due to its pervasiveness. Many software components, including those in popular open source logging tool Log4j, are the work of one or two developers who have little financial support. GitHub’s 2FA agenda aims to reduce the chances of bad actors compromising key open source projects through social engineering or similar account takeover attempts.
The staggered approach to implementing mandatory 2FA is calculated to ensure that everyone who needs to be onboarded does so of their own volition and in good time. GitHub’s rollout will begin on March 13th, targeting developers based on data points such as publishing frequency, whether they’re administrators at enterprises, and whether they contribute to more popular public and private repositories. Those targeted will receive an email and see a banner on their GitHub dashboard asking them to sign up, and they’ll have 45 days to activate 2FA. Regular prompts will encourage compliance during this period, and those who fail to set up 2FA within 45 days will be asked to enable it the next time they try to access their account.
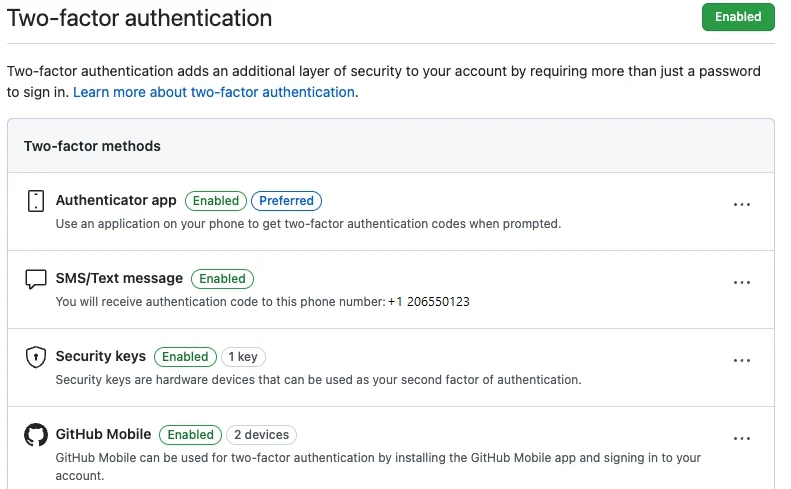
GitHub users can choose their 2FA mechanism from SMS, physical security keys, third-party authenticator apps, and the GitHub mobile app. GitHub advises people to activate more than one 2FA method as a fail-safe measure. The 2FA push won’t end with the initial enrollment, and those who have set up 2FA will receive another prompt after 28 days asking them to validate their 2FA method. This is designed to prevent developers from being locked out of their accounts due to a misconfigured authenticator app or mis-typed mobile phone number. If the user can’t authenticate their account at this stage, they will be asked to reset their 2FA method without losing access. After the initial rollout, GitHub plans to apply any lessons learned to the wider rollout throughout 2023.
GitHub Implements Staggered Rollout of Mandatory 2FA to Secure Software Supply Chain
GitHub 2FA in action. Image Credits: GitHub
GitHub, a software development platform with over 100 million developer users, has begun implementing mandatory two-factor authentication (2FA) to secure its software supply chain. In a calculated approach to ensure a smooth rollout, GitHub will target developers with the 2FA enrollment push gradually, allowing for adjustments and tweaks as necessary. The company emphasizes the importance of securing the software supply chain, which starts with the developer.
Developers who are targeted during this initial 2FA enrollment push will receive an email and see a banner on their GitHub dashboard asking them to sign up. They will have 45 days to activate 2FA, and regular prompts during that period to comply. If 2FA is not configured within this 45-day period, they will be prompted the next time they access their GitHub account. Those who still don’t comply will have no option other than to set up 2FA to access any part of their GitHub account.
GitHub users can choose their 2FA mechanism from SMS, physical security keys, third-party authenticator apps, and the GitHub mobile app. The company advises users to have more than one 2FA method activated as a fail-safe measure. After the initial rollout, those who have set up 2FA will receive another prompt after 28 days to validate their 2FA method, which is designed to prevent being locked out of their accounts.
GitHub plans to factor in various data points such as publishing frequency, administrative role, and contribution to popular public and private repositories to determine which developers can expect to start receiving 2FA prompts from March 13. The company will apply any lessons learned from this initial rollout to the wider rollout through 2023.

